Cisco ASA Remote Access IPSec VPN Configuration Step by Step
Today I am going to show you how to configure IPSec VPN on Cisco ASA firewall. The process is very easy so lets get started. In my case I am going to configure Cisco 5510 Series Adaptive Security Appliance (ASA) using the Adaptive Security Device Manager (ASDM).
Enter a name for the Tunnel Group Name. Supply the authentication information to use. such as Pre-shared Key
Choose whether you want remote users to be authenticated to the local user database or to an external AAA server group. Here I am using my Cisco ACS Server.
Define a pool of local addresses to be dynamically assigned to remote VPN Clients when they connect.
Click Next
Specify the DNS and WINS server information and a Default Domain Name to be pushed to remote VPN Clients.
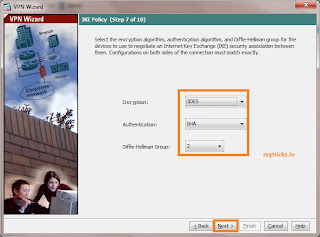
Specify the parameters for IKE, also known as IKE Phase 1. Configurations on both sides of the tunnel must match exactly. However, the Cisco VPN Client automatically selects the proper configuration for itself. Therefore, no IKE configuration is necessary on the client PC.
Specify which, if any, internal hosts or networks should be exposed to remote VPN users.
If you leave this list empty, it allows remote VPN users to access the entire inside network of the ASA.
This window shows a summary of the actions that you have taken. Click Finish if you are satisfied with your configuration.
Now open your Cisco VPN Client,
Attempt to connect to the Cisco ASA using the Cisco VPN Client in order to verify that the ASA is successfully configured.
Select Connection Entries > New.
Fill in the details of your new connection.
The Host field should contain the IP address or hostname of the previously configured Cisco ASA. The Group Authentication information should correspond to that used. Click Save when you are finished.
The remote VPN Client user authenticates against the Active Directory using a Microsoft Windows 2003 Internet Authentication Service (IAS) RADIUS server or Local User database.
Configure the ASA as a Remote VPN Server using ASDM,
Select Wizards > VPN Wizard from the Home window.Select the Remote Access VPN tunnel type and ensure that the VPN Tunnel Interface is set as desired.
Click Next.Enter a name for the Tunnel Group Name. Supply the authentication information to use. such as Pre-shared Key
Choose whether you want remote users to be authenticated to the local user database or to an external AAA server group. Here I am using my Cisco ACS Server.
Define a pool of local addresses to be dynamically assigned to remote VPN Clients when they connect.
Click Next
Specify the DNS and WINS server information and a Default Domain Name to be pushed to remote VPN Clients.
Specify the parameters for IKE, also known as IKE Phase 1. Configurations on both sides of the tunnel must match exactly. However, the Cisco VPN Client automatically selects the proper configuration for itself. Therefore, no IKE configuration is necessary on the client PC.
Specify which, if any, internal hosts or networks should be exposed to remote VPN users.
If you leave this list empty, it allows remote VPN users to access the entire inside network of the ASA.
This window shows a summary of the actions that you have taken. Click Finish if you are satisfied with your configuration.
Now open your Cisco VPN Client,
Attempt to connect to the Cisco ASA using the Cisco VPN Client in order to verify that the ASA is successfully configured.
Select Connection Entries > New.
Fill in the details of your new connection.
The Host field should contain the IP address or hostname of the previously configured Cisco ASA. The Group Authentication information should correspond to that used. Click Save when you are finished.